Cybersecurity in Centralized Vs. Decentralized Computing
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best practices.
In the early phase of using computers in industrial settings, their requirements were very limited. Today, with the widespread use of IoT devices in numerous industries, data is abundant. Computing power is required to process the vast amount of data generated, often requiring large central computing systems or multiple distributed systems.
These systems also have cybersecurity implications associated with them. Before discussing various computing systems and their cybersecurity implications, it is important to know the difference between operational technology (OT) and information technology (IT) in the IoT realm.
Operational Technology vs. Informational Technology (OT vs. IT)
As the names indicate, OT deals with the operational side of a manufacturing facility, and IT deals with the information side. The hardware and software used to control and monitor processes in a facility are operational technology.
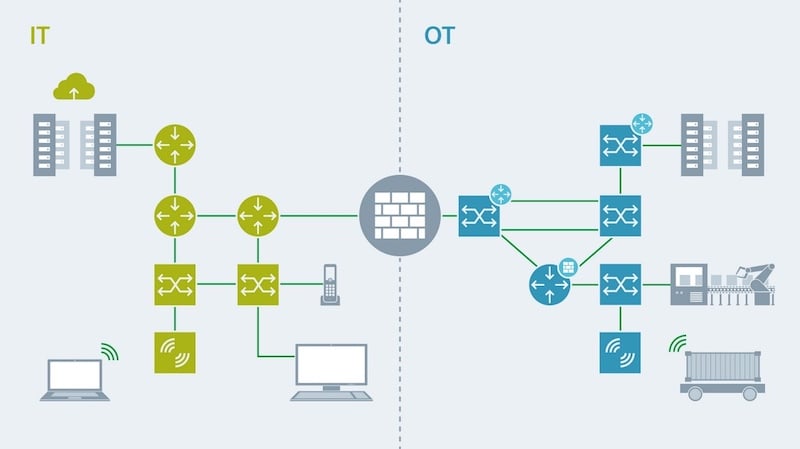
Figure 1. A diagram showing the differences between IT and OT concepts. Image used courtesy of Siemens
In industrial control systems (ICS), SCADA, PLCs, sensors, and other devices that have specific functions to monitor or control other equipment in operation are part of OT. They perform certain actions in a pre-programmed manner to achieve the desired outcome in plant operations.
On the other hand, IT deals with data and information flow. It deals with the hardware and software that provides supporting technology for industrial operations. This could range from email services to manufacturing execution systems (MES). Such IT systems are not always critical to plant operations but can enhance plant operations by improving efficiency.
Centralized vs. Decentralized Computing
Network systems across the world operate in a centralized fashion. A single server acts as the node to store, process, and route information across the whole network. There will only be one server at the center to which all the devices are connected. Other users and devices will be able to access the information from the central server with authorized access. But this mode of centralized computing has been replaced by decentralized computing systems.

Figure 2. An example of centralized computing. Image used courtesy of Loyola University Chicago
There is no single server at the center in decentralized computing systems, but there are interconnected clusters with a node at their centers. These nodes are connected. Computing power is not limited to a central server but is spread across many nodes. This is a much more efficient operation model, as the possibility of a fault taking down the whole system is very low.
An extension of decentralized computing is the distributed computing model. In this model, all the devices have computing capabilities and are connected to all other devices by a mesh network. In the mesh network, there is an enormous number of routes for the data to travel. It is a more resilient computing architecture but comes at a higher cost.
Cybersecurity Challenges in Computing
Cybersecurity threats to industrial systems are rising in recent years, as is evident by the recent attacks on the critical infrastructure of national interests. Hackers were able to hold entire pipelines at ransom in some instances. Protection from cyberattacks has to be thought of for every computing system used in conjunction with automation and IoT.
In a centralized computing model, the central server is the key vulnerability. If the central server is compromised, the whole system goes offline, and the operations can be halted. A single point of attack can bring down the complete system. Importance has to be given to protect the central server.
In a decentralized and distributed model, the attack vector is much wider. Even if one of the nodes or devices is compromised, the rest of the system can remain operational.

Figure 3. An example of centralized vs. decentralized in the context of computing. Image used courtesy of Adam Aladdin [CC BY-SA 3.0]
Also, if identified, the affected part of the system can be severed off while the rest of the system remains operational. But if the security breach goes unidentified, malware can spread across the network and infect all nodes and devices.
IoT has also changed the cybersecurity landscape for industrial systems. The centralized model in IoT architecture uses central servers, and the distributed model relies on edge computing. All the devices are connected to the internet and have some level of data processing capabilities. This increases the potential attack vectors for hackers. IoT infrastructure in every architecture is hugely vulnerable to attacks, and best cybersecurity practices must be followed to safeguard critical infrastructure.
Cybersecurity Best Practices
Industrial systems are becoming more vulnerable to attacks by sovereign opponents and malicious attackers. The best option to avoid such attacks is to build defense systems in place. The National Institute of Standards and Technology (NIST), along with the International Society of Automation (ISA), have laid down guidelines and standards for cybersecurity for industries. Some of the best practices to be followed to build a resilient ICS are given below.
Industrial Firewalls, Encryption, and Redundancy
The firewall provides network security by constantly monitoring the data that flows through the network. It is a system that uses both hardware and software technology to prevent cyberattacks. They block and divert traffic based on a predefined set of rules for the network. A firewall implemented by vendors with a proven track record has to be the first line of defense for every ICS implementation.

Figure 4. A multi-port industrial firewall with enhanced security features that comply with utility and industrial standards. Image used courtesy of ABB
Data exfiltration is one of the major cybersecurity challenges businesses have to face. All communication through the network has to be encrypted. Data encryption protects the information even if the data was hijacked from the network and serves as an additional layer of security to protect sensitive information.
Redundancy has to be built into the system to increase resilience. Backups ensure business continuity even after a cyberattack occurs by storing the data at a central server that is regularly backed up in different locations. Such backups can restore data when cyberattacks decimate the data stored at the central server.
Passwords, Authentication, and Security Updates and Audits
One of the most common entryways for hackers is using common passwords. Some facilities forget to change the default passwords that vendors ship with their devices and software. Strong passwords should be used, and corporate password management solutions can be helpful in that regard. Two-factor authentication or multi-factor authentication can be used to add an extra layer of security to the network.
Cybersecurity is constantly evolving. New modes of attacks and new vulnerabilities are exposed regularly. Device manufacturers release software updates and patches for their devices. The firm should promptly apply such updates and patches to have up-to-date protection. Vendors that provide regular updates have to be chosen in the first place.
External agencies conduct security audits to test the strength of the company’s cybersecurity defenses. During a security audit, penetration testing and various other techniques are used by white-hat hackers to break down the defenses. This exercise reveals the system’s vulnerability and can improve the cyber resilience of the ICS.
All forms of computing systems are vulnerable to cyberattacks. They evolve constantly, and the defenses against them also have to evolve accordingly. Cybersecurity is a constant effort by the industries to stay on top of newer methods of attack.